Chrome has a malware problem
 Google Chrome extensions are designed to improve or modify functionality that the web browser offers. Some extensions in the official Chrome Web Store have millions of users who all rely on the functionality their add-ons provides them with.
Google Chrome extensions are designed to improve or modify functionality that the web browser offers. Some extensions in the official Chrome Web Store have millions of users who all rely on the functionality their add-ons provides them with.
While not as powerful as Firefox add-ons, Chrome extensions are easily powerful enough to manipulate websites that you visit, or communicate with a remote server. News about extension abuse reached the mainstream press recently.
It all started when Amit Agarwal confessed that he sold a Chrome extension he created to a company that approached him via email.
The company modified the extension and released the update to all existing users of it.
Users who received the update noticed that the extension started to inject ads on web pages, which was then reflected on the user reviews page on the Chrome Web Store.
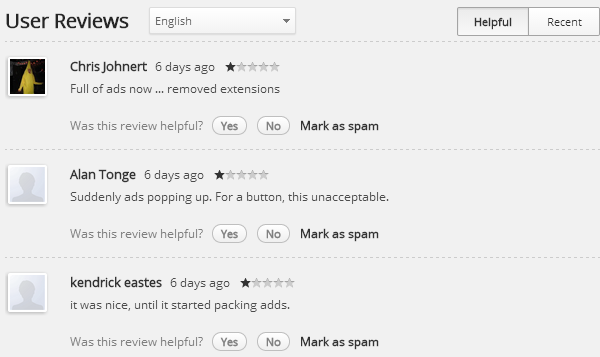
Amit's extension was not the first to be sold to a company, and it is likely that it won't be the last. While buying extensions to add monetization options to it appears to be a popular choice, it is not the only one available.
About ten months ago, the developer of the popular HoverZoom extension agreed to integrate code into the extension that would report back to a media consulting company.
So how can this happen?
The Chrome Web Store policy defines what extensions can and cannot do. According to that policy "extensions must have a single purpose that is narrow and easy-to-understand".
This policy is only enforced on new extensions currently, and will become enforced on existing extensions in June 2014 according to a Chromium blog post addressing the change.
While that leaves a lot to interpretation, the example given sheds some light on what is now allowed.
For example, functionality that displays product ratings and reviews, but also injects ads into web pages, should not be bundled into a single extension.
This is probably the reason why the extension that Amit sold to the company was removed from the store by Google.
Removal is a manual process, and one that is used when abusing extensions are reported to Google.
Extension submissions to the Chrome Web Store, however, are automated. They are scanned for malware but not reviewed by Google before they become available. This is different to how Mozilla handles that on AMO.
While add-ons may be listed on the Firefox Add-ons repository prior to a full review, only a full review enables additional privileges such as automatic updates.
Chrome extensions installed from the store get updated automatically, and usually without notification unless they require additional rights. If that is the case, a message is displayed to the user.
It is almost impossible for users to find out what has changed in an update, or if an extension that they are interested in contains ad-injecting or otherwise harmful code.
While some may be able to review the code of an extension, most are probably not that versed in JavaScript to do so. In addition, minification and obfuscation increase the difficulty of it further.
For some, it may even be problematic to identify the extension that is causing the behavior. If you have ten extensions installed, it may be difficult to find out which is causing the issue.
One of the better ways to handle this is to turn off all extensions to check each individually until the culprit is found.
What Google should do
Google needs to improve its store policy further. One of the first things that would help is to visually indicate extension ownership changes.
This is not indicated anywhere on the Chrome Web Store right now. While a change in ownership does not necessarily mean that monetization options are integrated into the extension, it informs users about the change so that they can be more careful when it comes to it.
Automatic scanning does not pick up on extensions that do inject ads on websites or phone home to remote servers currently.
A manual review system similar to the one that Mozilla is using would ensure that these extensions or updates won't be released to the store.
Source: Betanews
